Here Comes a New Challenger – Conti Ransomware
Published on 14 Jul 2021 | Updated on 14 Jul 2021
CyberSense is a monthly bulletin by CSA that spotlights salient cybersecurity topics, trends and technologies, based on curated articles and commentaries. CSA provides periodic updates to these bulletins when there are new developments.
OVERVIEW
According to Coveware (a cybersecurity firm which specialises on ransomware incident response), Conti ransomware has emerged as the second* most common ransomware observed in ransomware attacks for 2021Q1. The Conti ransomware first appeared in May 2020 and had affected more than 400 organisations worldwide. The Conti cybercriminal group specifically targeted organisations that provide essential services, such as hospitals, emergency medical services, and 911 dispatch carriers, demanding exorbitant ransom amounts knowing that these organisations can ill-afford to operational downtime in the backdrop of the COVID-19 pandemic. One of the recent incidents highlighted in the last edition of CyberSense saw Conti ransomware wreak havoc on Ireland’s Health Service Executive (HSE). This edition of Cybersense takes a closer look at Conti ransomware group and some of the observed tactics and techniques it has utilised.
* The Revil (also known as Sodinokibi) ransomware is the most common ransomware family observed in 2021Q1. Refer to the CyberSense edition on Revil Unravelled for more details.
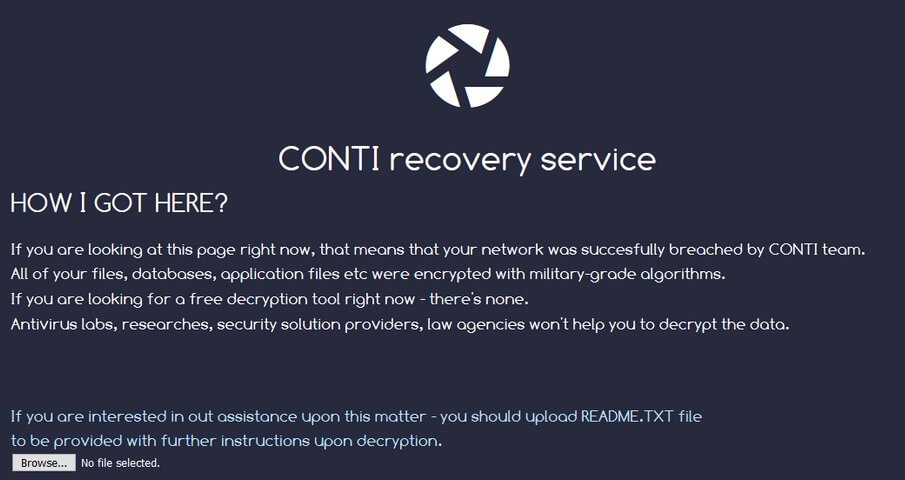

POLISHED TO PERFECTION – A CONGLEMERATION OF DIFFERENT TACTICS AND TECHNIQUES
Ruthless and ‘Wicked’ OperatorsConti ransomware is identified to be a possible successor for Ryuk ransomware, due to similarities in its code and distribution tactics. Both reportedly share the same creator and distributor – Wizard Spider, an established and sophisticated cybercriminal group. Like Ryuk – which is still in use - Conti ransomware was also ruthlessly used to target the healthcare sector and related essential emergency services during the pandemic. This is unlike some ransomware groups who declared that they would steer clear of targeting healthcare services in this crucial period.
Simple, yet Effective Intrusion Vectors
Like many ransomware groups, Conti ransomware is offered through a Ransomware-as-a-Service (RaaS) model, where trusted affiliates are granted access to its infrastructure to conduct ransomware attacks without the need to develop native capabilities.The ransomware typically gets delivered through phishing, remote desktop protocol (RDP), or exploiting unpatched software. The group often uses phishing which comes in seemingly innocent Microsoft Word documents with malicious macros, or legitimate Google document URLs with malicious links. These delivery techniques are simple but effective, especially as cyber hygiene remains a concern for many organisations, given the shift to remote-working arrangements amid the COVID-19 pandemic. Conti ransomware group recognises this, as it targets private home networks and work-from-home employees to comprise networks.
Weaponising Existing Toolkits and Retaining Manual Control within Victim Networks
Upon gaining initial foothold in an organisation, Conti ransomware group weaponises tools, such as penetration testing software Cobalt Strike, to conduct reconnaissance, move laterally across networks, and finally deploy the ransomware. These malicious activities are mostly “human-operated” for the Conti ransomware group, which demonstrates the sophistication of these operators and their extensive knowledge of victim organisations’ systems, possibly allowing them to adapt their strategy and tactics according to their discovery within the compromised network.
Rehashing Popular Post-compromise Strategies
Like many prominent ransomware groups, the Conti ransomware group also uses the “double extortion” tactic. This tactic adds pressure to victims on top of locking up their files, by threatening to leak the stolen data from the victims if the ransom demands are not acceded. As large enterprises and healthcare institutions hold valuable troves of personal information of their customers or patients, this may cause significant reputational damage for victim organisations, and even run the risk of lawsuits and litigation damages.
Targeting Critical Infrastructure Victims for Larger Pay-Outs
Conti ransomware have targeted critical infrastructure healthcare and government sectors with devastating effect. Victims of Conti ransomware attacks include the Ireland’s HSE, City of Tulsa (including their City Council and Police), Broward County Schools, as well as reportedly at least 16 U.S. healthcare and first-responder networks. The FBI had also issued an alert over increased Conti ransomware attacks targeting healthcare systems, government, law enforcement and critical infrastructure agencies – organisations that are not able to afford operational down-times. Based on statistics by Coveware, the average Conti ransom payment for the month of June 2021 amounted to SGD1.15 million, compared to the generic ransomware’s average ransom payment of SGD300,000. This is the main reason the Conti ransomware group target organisations that provide essential services as they hope to collect larger pay-outs.
KEY TAKEAWAYS
In summary, there has been a dramatic shift in the threat posed by ransomware, from sporadic and isolated, to massive and systemic. The scale, brazenness and impact of ransomware attacks have also soared as observed in the increase in ransomware attacks targeting essential service providers (e.g. Colonial Pipeline, HSE). These incidents have demonstrated that even ‘simple’ ransomware attacks can have significant cyber-physical impact, with severe downstream consequences. In addition, the recent ransomware incident involving exploitation of the vulnerability in the Kaseya Virtual System Administrator – a popular platform among managed service providers (MSPs) – allowed cybercriminals to use affected MSPs as conduits to infect a larger pool of connected clients. The attack has illustrated that ransomware attacks can also have downstream effects through service providers, making it an even more potent threat.Among the various types of malicious cyber activities, ransomware is emerging as a clear and present threat to enterprises, regardless of big or small. Organisations will need to take preventative measures to mitigate the risks and be prepared to deal with a ransomware incident, before it occurs. For more information on preventive measures against ransomware, please refer to SingCERT advisory on Ransomware: A Growing Cybersecurity Threat to Businesses.
REFERENCES:
Malwarebytes, CPO Magazine, ZDNet, Security Magazine, Coveware