A Closer Look At Wiper Malware
Published on 18 Jul 2022 | Updated on 18 Jul 2022
CyberSense is a monthly bulletin by CSA that spotlights salient cybersecurity topics, trends and technologies, based on curated articles and commentaries. CSA provides periodic updates to these bulletins when there are new developments.
OVERVIEW
Wiper malware is a relatively new but highly destructive class of malicious software, first observed to have been used in the Middle East in 2012. During the Russia-Ukraine conflict in 2022, wiper malware emerged as a popular cyber weapon of choice for threat actors.
In this edition of CyberSense, we will dive deeper into the class of wiper malware, explore the recent rise in observations of cyber-attacks involving new wiper malware strains, and discuss how organisations can better defend themselves against these attacks.

Figure 1. A graphical illustration of data-erasing wiper malware
WHAT IS WIPER MALWARE?
At first glance, wiper malware share some similarities with its equally - or more infamous - sibling, ransomware. Both types of malware involve making files and data inaccessible to the victim. Some wiper malware variants may also deliberately masquerade as ransomware by demanding “ransom” fees from its victims.
However, unlike ransomware - which encrypts its victim’s data, temporarily denying access until the ransom is paid - wiper malware typically aims for destruction or to cause permanent loss.
The use of wiper malware is therefore usually not financially motivated – experts believe that wiper malware is mainly used by threat actors to cover their tracks after exfiltrating information from a network, or to cause outright disruption.
HOW DOES IT WORK?
Broadly, there are two mechanisms that wiper malware employ:
- Overwriting system components, such as the Master Boot Record[1] (MBR) or the Master File Table[2] (MFT). This cripples the operability of the victim’s computer and prevents information from being accessed, although file contents remain untouched and may still be recoverable.
- Overwriting or encrypting files, along with any backups found on the computer, to permanently delete the victim’s data and information.
Threat actors today typically incorporate a mix between the two approaches to achieve the greatest damage in the shortest amount of time possible.
Wiper malware ranks among one of the most destructive classes of malicious software that hackers may employ. Such attacks on an organisation’s Information Technology (IT) systems could disrupt IT-dependent business operations extensively, and lead to losses of valuable data and information. Attacks on Operational Technology (OT) systems - such as those underpinning transportation systems or energy grids - could cause even greater damage by disrupting industrial systems and equipment, resulting in devastating effects and endangering lives.
One of the first wiper malware attacks observed was Shamoon, which emerged in 2012 when it was used in a disruptive attack against Saudi Arabia’s state-owned national oil company Saudi Aramco. Public reports suggest that Shamoon had been unleashed by a company insider with privileged access to Aramco’s network. Once a machine had been infected, Shamoon would erase the data on its hard drives and replace them with an image of a burning American flag. The malware infected over 30,000 computers, which were rendered useless and had to be replaced. Aramco was forced to shut down its internal corporate network to stop the virus from spreading. Researchers speculate that Shamoon could have been a copycat inspired by a similar malware Wiper that hit some Iranian networks earlier that year.
Some types of wiper malware are designed with the ability to autonomously propagate – or ‘worm’ – throughout a compromised network by spreading copies of itself from computer to computer without any human interaction. These variants are particularly dangerous, as they are extremely difficult to contain once they have been let loose, and can result in wide-reaching rippling effects worldwide.
An example of the destructive potential of self-propagating wiper malware can be seen in NotPetya. In 2017, researchers started to notice this self-propagating wiper malware infiltrating the networks of Ukrainian organisations. NotPetya had masqueraded as ransomware by demanding “ransom” fees from users, but in reality lacked a ransom recovery mechanism. With its ability to worm across different systems via a vulnerability in the Windows system, NotPetya quickly spread beyond its original targets, eventually crippling some of the largest corporations worldwide, including international shipping giants Maersk and FedEx, pharmaceutical company Merck and construction company Saint Gobain. According to estimates from the White House, the total damages from NotPetya in 2017 reached US$10 billion, making it the most financially damaging cyber-attack to date.
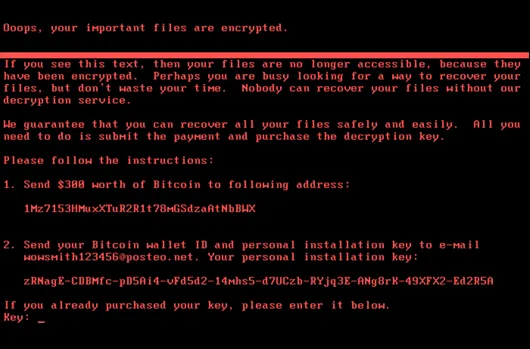
Figure 2.A screenshot of NotPetya’s “ransom note”, which states that users could recover their data after making a ransom payment. In reality, this was untrue as NotPetya was a wiper malware that lacked a decryption mechanism. (Source: CrowdStrike)
Other types of malware may include wiper capabilities as just one among many functionalities within their arsenal. In April 2022, researchers revealed the existence of the INCONTROLLER (aka PIPEDREAM) malware framework, which had been specifically developed by threat actors to disrupt industrial processes. The deadly malware, which has been described by researchers as a “Swiss Army Knife” for industrial system cyber-attacks, includes an expansive array of components that can target devices, disrupt or prevent operators from accessing them, permanently brick them, or use them as a foothold to access other parts of the network. The adaptability and multi-functionality of INCONTROLLER meant that it could pose a threat to almost all types of industrial systems around the world. Fortunately, researchers discovered the malware, and started constructing defenses against it, before it could be used for disruptive or destructive attacks.
ROLE OF WIPER MALWARE IN RUSSIA-UKRAINE CONFLICT
Since the start of the Ukraine-Russia conflict in late February 2022, researchers have observed a spike in new wiper malware variants used in cyber-attacks. Ukrainian security officials have reportedly identified at least eight types of wiper malware[3] used by hackers to attack Ukrainian entities, including government agencies, banks and utilities companies.
The current wave of attacks mostly involve non-self propagating wiper malware, and appears to be targeted specifically at Ukrainian entities. However, the effects of some attacks have still been felt beyond Ukrainian borders. For instance, in the cyber-attack on US satellite communications provider Viasat’s KA-SAT network on 24 February 2022, tens of thousands of modems were reportedly rendered inoperable by the AcidRain wiper malware. The attack disrupted internet connectivity for tens of thousands of Viasat’s customers across Ukraine and Europe, even disrupting the remote monitoring and control of 5,800 wind turbines in Germany.
KEY TAKEAWAYS
The rising prevalence of new wiper malware variants during the Russia-Ukraine conflict represents a potential cyber threat to organisations worldwide. Wiper malware is destructive – it can wreak havoc by crippling systems and destroying valuable data. It creates permanent damage to systems – files damaged by wiper malware cannot be recovered. It can also affect systems indiscriminately when the malware possesses self-propagation mechanisms. As hackers unleash more new variants of wiper malware into the ecosystem, there is a risk that one of the variants could spread out of control, leaving behind a global trail of devastating destruction (as in the case of NotPetya).
While there have not been reports of any threats to Singapore organisations in relation to the events in and around Ukraine, organisations are encouraged to take the necessary precautionary measures to defend themselves against wiper malware attacks amidst their intensified use. These measures are similar to those to defend against ransomware. For example, organisations may consider:
- Enforcing best practices, such as creating regular offline and off-site backups; and
- Imposing network monitoring and reviewing system logs to ensure swift detection of anomalies and prevent widespread damage should a breach occur.
For more information on how to strengthen your cybersecurity posture amidst the Russia-Ukraine conflict, please refer to the CSA advisory here.
SOURCES INCLUDE:
CISA, Cyber Law Toolkit, DarkReading, Dragos, ESET, Fortinet, InfoTransec, Mandiant, MIT Technology Review, Norton, SecurityIntelligence, The Record, Viasat, Wired
[1] The MBR is a crucial section of the computer’s storage that instructs the computer how to boot up.
[2] The MFT is a file directory that stores information such as where the files are located and the format of the files.
[3] These include AcidRain, WhisperGate, WhisperKill, HermeticWiper, IsaacWiper, CaddyWiper, DoubleZero, and Industroyer2.