Hacktivism during Military Conflict: The Anonymous Hacker Collective
Published on 09 Mar 2022 | Updated on 09 Mar 2022
CyberSense is a monthly bulletin by CSA that spotlights salient cybersecurity topics, trends and technologies, based on curated articles and commentaries. CSA provides periodic updates to these bulletins when there are new developments.
OVERVIEW



On 24 February 2022, Russia launched a large-scale invasion of Ukraine. Amidst the international outcry against the military offensive, hacker groups were observed to pick sides, carrying out cyber attacks against organisations in one country on behalf of the other. Checkpoint Security had observed, however, that numerous hacks that these groups claimed to have executed were either false or insignificant, and that the groups appear more focused on “building self-reputation and receiving credit” for supporting either combatant than causing real damage.
Nonetheless, several claimed hacks were verified, among them the handiwork of the hacktivist group Anonymous. Since declaring cyber war against Russia, the hacker collective has claimed credit for infiltrating the Russian Ministry of Defence database, carrying out distributed denial-of-service (DDoS) attacks on Russian government websites, and hacking multiple state TV channels to show pro-Ukraine content. This makes Anonymous one of the more technically skilled – and dangerous – hacker groups to have joined the current conflict.
In this edition of CyberSense, we look into the origins and motives of the Anonymous Collective, their tactics and techniques, key incidents they have been responsible for through the years, and what organisations can do to protect their networks during times of geopolitical tension.
From Pranks to Hacktivism
The Anonymous Collective claimed to have grown from the idea that a decentralised international group of hacktivists could band together, without a leader, against government bodies and corporations around the world that were deemed to have gone against their philosophies. Its members’ ideologies vary and can be wildly different, but often revolve around the opposition of internet censorship and control, as well as taking action on geopolitical issues and human rights violations in accordance with their own ambiguous and often vacillating moral code.
However, Anonymous was not always associated with hacktivism. First introduced in 2003 within the imageboards of ‘4chan’, Anonymous users on the forum started to jokingly act as if they were part of a single entity, and conducted mass pranks or raids as they flooded targeted websites with unwanted traffic. It was only in 2008 when Anonymous launched Project Chanology that the group started to deviate from their usual acts of ‘mischief’ and engage in politically-motivated hacking. In February that year, supporters of the Anonymous collective gathered around physical locations of the Church of Scientology facilities, protesting against what they perceived as Internet censorship by the Church, whilst donning the now-famous ‘Guy Fawkes’ mask, popularised by the film ‘V for Vendetta’. As the years went by, Anonymous became increasingly emboldened as they targeted major corporations such as PayPal and various law enforcement agencies for their part in rooting out piracy.
Anonymous: Tactics, Techniques, and Prominent Campaigns
The most prominent campaigns by Anonymous often saw distributed-denial-of-service (DDoS) attacks, website defacements, and data leaks, mainly keeping their presence online, save for a few physical on-the-ground demonstrations on ‘November the Fifth’s*. Declarations of cyber war or intent were commonly made through videos – released on YouTube - of a man in a ‘Guy Fawkes’ mask reading a message with voice-changing tools. Various open-source DDoS tools were also made readily available online by Anonymous, complete with detailed examples and instructions for use, allowing for even unsophisticated actors to join in their ‘causes’.
*November 5th refer to ‘Guy Fawkes Night’ as it marks a commemorative public holiday in Great Britain for the Gunpowder Plot’s failure of assassinating Protestant King James I by Catholic plotters.

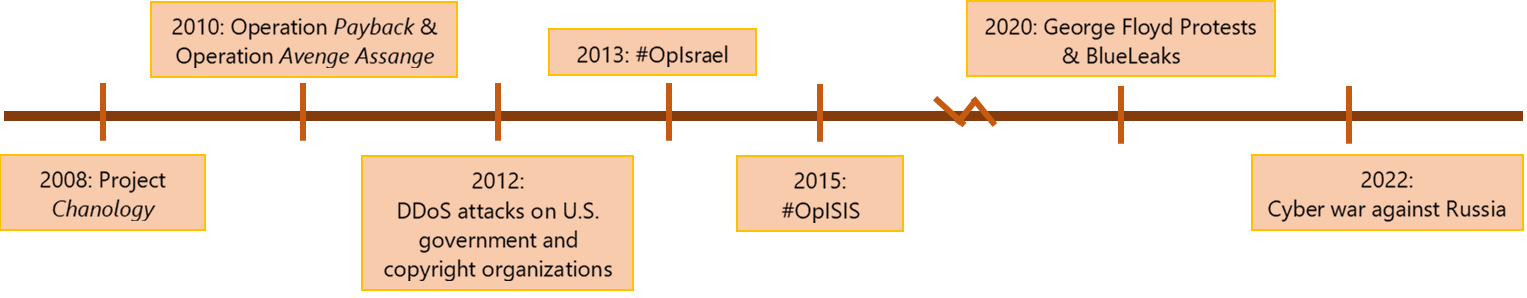
Prominent campaigns by Anonymous in the past include:
2008, Project Chanology: The Church of Scientology issued a cease-and-desist letter for violation of copyright to then-Gossip blog Gawker as the latter refused to take down a satirical video in which devout Scientologist Tom Cruise praised the virtues of Scientology, overlayed by music from Cruise’s Mission: Impossible films. Anonymous perceived this as a threat to Internet dissent and threatened to “expel the church from the Internet”. A series of DDoS attacks hit Scientology websites and flooded Scientology centers with prank calls and fax transmissions.
2010, Operation Payback & Operation Avenge Assange: In response to a crackdown on piracy websites, Anonymous launched multiple DDoS attacks on websites of copyright-stringent organisations Motion Picture Association of America (MPAA), International Federation of the Phonographic Industry, as well as their affiliates. Operation Avenge Assange shortly followed in December 2010 as various payment companies froze donations to WikiLeaks due to mounting political pressure to recognise WikiLeaks as a national security threat. In this campaign, Anonymous launched DDoS attacks against PayPal, MasterCard, and Visa websites, causing a minor slowdown to PayPal’s service.
2012, DDoS attacks on U.S. government and copyright organizations: Similar to Operation Payback in 2010, Anonymous retaliated to the shutdown of the file sharing service MegaUpload by law enforcement agencies and targeted the websites of copyright organisations and various government bodies within the U.S. with DDoS attacks. These include the United States Department of Justice, the United States Copyright Office, the Federal Bureau of Investigation, and MPAA.
2013, #OpIsrael: In April 2013, Anonymous began their annual hacking operation on Israel’s Internet infrastructure with website defacements and attempts at data exfiltration and DDoS attacks. The hacker group’s goal is to “erase Israel from the Internet”, and was launched on the eve of Holocaust Remembrance Day every year. However, attempts seemed to have died down in recent years as security experts have since deemed the operation a “failure” with limited impact to Israel.
2015, #OpIsis: Following the November 2015 Paris attacks by ISIS, Anonymous declared that they would hunt down and dox ISIS members and its affiliates around the world. As part of their campaign, brute-force attacks to gain control of pro-ISIS social media accounts and DDoS attacks on public Islamic State websites were commonplace for more than a year.
2020, George Floyd Protests & BlueLeaks: The murder of George Floyd by a white Minneapolis police officer caused public outrage. After being relatively quiet in the preceding years, Anonymous re-emerged, launching a wave of DDoS attacks on the Minneapolis police department website and defacing a minor United Nations agency website as a memorial for Mr. Floyd. 269 gigabytes of internal police files from more than 200 agencies across the U.S. were also leaked, exposing personal data of 700,000 police officers.
What Organisations can do to Protect their Networks
Although many persons whom oppose the military offensive have cheered Anonymous as they carried out hacking sprees, hacktivist groups are often unpredictable, and can change their activities and targets on a whim – an outcome of their wildly different ideologies. While their declared motives may also sound noble at times, the fact remains that many ordinary people are affected by their activities. For example, service disruptions - such as in the case of PayPal - greatly inconvenienced users, and had trickle-down effects for other consumers. ‘BlueLeaks’ exposed personal data of many innocent police officers unrelated to George Floyd’s murder, affecting them and their families. Indeed, many members of the Anonymous collective had been arrested due to their involvement in these hacktivist activities.
Considering the large number of hacker groups that have joined in the cyber-attacks on both Ukraine and Russia, organisations are advised to take active steps to strengthen their cybersecurity posture to avoid collateral damage in the ongoing conflict. Understanding the tactics and motives of hacker groups can help combat and mitigate said threats, especially during periods of tension. Organisations and government entities should diligently patch website vulnerabilities and engage appropriate vendors and DDoS mitigation tools to prevent disruptive attacks from cybercriminal groups.
For further details and mitigation measures, please refer to SingCERT’s advisory on actions to strengthen your cybersecurity posture amidst of developments in the Russia-Ukraine conflict.