Killnet - From Cybercriminals to Cyber-Partisans
Published on 25 Oct 2022
CyberSense is a monthly bulletin by CSA that spotlights salient cybersecurity topics, trends and technologies, based on curated articles and commentaries. CSA provides periodic updates to these bulletins when there are new developments.
OVERVIEW
As the Russia-Ukraine conflict progressed, hacktivism slowly took centre-stage, with many hacker groups taking sides and providing support for the cyber-conflict. Prominent groups included the pro-Ukraine Anonymous collective (click here for the past Cybersense issue on “Hacktivism during Military Conflict: The Anonymous Hacker Collective”), which admonished and carried out various hacks on Russia-linked organisations.
There were also pro-Russia hacktivist groups that retaliated against countries that they felt were acting in an “unfriendly” manner towards Russia. Killnet is one such group. Since declaring their participation in the conflict, Killnet has grown to encompass a sizeable following. In this issue of Cybersense, we dive into the background of Killnet, identifying their origins and notable campaigns since their inception. We also look at how they have evolved, their common Tactics, Techniques and Procedures (TTPs), and how organisations may guard against hacktivist groups in general.
EVOLUTION OF GROUP AND RECRUITMENT
Killnet describes themselves as a decentralised, uncontrolled “army of cyber partisans” from all over the world. Killnet did not start off as a hacktivist organisation, but was in fact a cybercriminal group advertising DDoS [1] for-hire services. The tool was first made available on a subscription basis in January 2022; users would pay US$1,350 a month to access it. With a click, they could perform Layer 3, 4 or 7 DDoS attacks [2], with a capacity of 500 Gbps across 15 computers, all through a simple graphical user interface.
With the inception of the Russia-Ukraine conflict, Killnet transformed itself from a criminal service provider to a hacktivist group, motivated by a declared mission to “stop the aggression against Russia”. Between March and September 2022, Killnet gained notoriety for targeting organisations within countries that have either supported Ukraine or have taken actions deemed detrimental to Russia’s interests.
Recruitment strategy
Killnet’s exploits and declared mission have been divisive, even within Russia; although some citizens condemn their actions, others praise the group for “defending the nation”. Cybersecurity firm Digital Shadows described Killnet as actively recruiting suitable candidates from supporters of the invasion, by leveraging various social media channels (e.g. Telegram, VK [3], etc.). Killnet has since deployed these “volunteers” to crowdsource attacks against targets.
This is not to say that Killnet accepts anyone into its ranks; in fact, researchers have observed the group imposing multiple minimum requirements on would-be recruits. Hackers who wish to join must have prior experience and some credibility (e.g. past cybersecurity exploits to their name), whereas other hopefuls, like graphic designers and programmers, must be accomplished in their field. Strict rules are set out for every member, with the punishment for violating them being expulsion from the group. In certain cases, recruits even have to fill in a detailed form before they are considered.
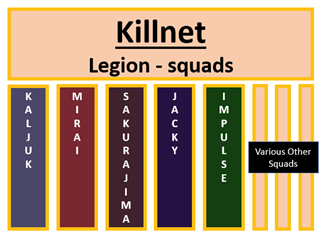
Figure 1. Diagram of Killnet Hierarchy, with Killnet command at the top giving orders to multiple smaller sub-groups
Analysts describe Killnet as having a well-structured operation; with a military-like structure that has a clear top-down hierarchy. Within Killnet, there are multiple smaller squads which act upon instructions given out in their Telegram channels, where they are said to have up to 100,000 followers. These squads, which Killnet calls their “Legion”, have demonstrated some level of coordination in their attacks, usually taking the instructions passed out through Telegram. This structure has proven effective, as Killnet continues to recruit members and increase their number of squads.
PROMINENT CAMPAIGNS
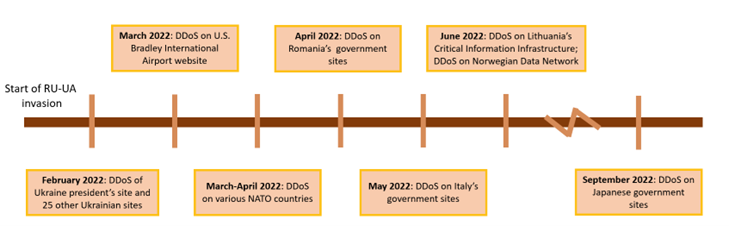
Figure 2. Timeline of Prominent Incidents over 2022
February 2022, on Ukraine government websites: Websites of Ukrainian government organisations were taken down, including the website of the Ukraine president. This was believed to be Killnet’s first attack in retaliation against what they perceived as “aggression against Russia”.
March 2022, on US Bradley International Airport website: Killnet brought intermittent downtime to the website of Bradley International Airport, claiming that this attack was in response to US “supplying weapons to Ukraine”, and claimed they will continue to attack US’ critical information infrastructure (CII) unless the latter ceased doing so.
March - April 2022, on various NATO countries: Killnet claimed responsibility for DDoS attacks against government and private organisations within NATO countries and European organisations. Affected countries included the Czech Republic, Estonia, Germany, Poland, the UK, and the US. The websites of the United Nations, the Organisation for Security and Cooperation in Europe (OSCE), and NATO’s Cooperative Cyber Defence Centre of Excellence (CCDCOE) in Estonia were also affected.
April 2022, on Romania’s government sites: Killnet launched a series of DDoS attacks targeting several Romanian government websites, resulting in hours of downtime. A statement issued by the Romanian National Directorate of Cyber Security (NDSC) mentioned that the affected sites included the official Romanian government and Ministry of Defence websites.
May 2022, on Italy’s government sites: After Killnet announced plans to attack Italy-linked entities, such as banks and firms in the media and energy sectors, multiple Italian news outlets reported outage of various online portals, which included that of the Italian Ministries of Foreign Affairs and Defence.
June 2022, on Lithuanian organisations: Lithuania’s National Cyber Security Centre (NCSC) warned of ongoing DDoS attacks against their National Cyber Data Transfer Network, government institutions and private companies. Shortly after, Killnet claimed responsibility for the attacks and threatened to launch further attacks unless Lithuania “lifted the barricade” [4].
June 2022, on Norwegian data network: Just two days after the attacks against Lithuania, Norway’s National Security Authority (NSA) announced that several institutions had their services rendered offline for a few hours, blaming an unnamed “criminal pro-Russian group”. Notably, the attack occurred hours after Norwegian officials strongly encouraged NATO to adopt Finland and Sweden as members at the Alliance’s 2022 NATO Summit.
September 2022, on Japanese government sites:The websites of several Japanese organisations, such as the country’s online tax portal and web gateway for government applications, were attacked by Killnet. This made Japan the first Asian country to be hit by Killnet’s DDoS attacks. Killnet claimed that the reason for this attack was for Japan’s “militarism”.
TTPS & PROMINENT CHARACTERISTICS
The Killnet group has displayed several unique TTPs and characteristics in their operations. These include:
Relatively unsophisticated, quick-burst attacks. Despite the high tempo of their disruptive campaigns, Killnet’s attacks are comparatively low-level, reaching average volumes of 40-100 Gbps and lasting 1-2 days. Considering that modern large-scale DDoS attacks can now flood targeted systems with several Terabytes per second, many organisations targeted by the attack were generally able to restore their systems within several hours, after appropriate mitigation measures kicked in.
Social media savviness. Killnet appears to be extremely attuned to social media. In particular, the group would often discuss their attacks and exploits on platforms like Telegram and VK [3]. The group also tends to announce targets over its Telegram chat channel to crowdsource attacks, a practice it has generally followed since the group’s inception.
Targeting of government websites. So far, countries hit by Killnet’s attacks fall into one of the following categories: (i) countries that have applied to join NATO; and (ii) those that have impeded Russia’s war effort directly or indirectly. From websites that host vital services to the public, and to those of various political parties, Killnet has on multiple occasions targeted government sites. Analysts speculate that these attacks are both to signal displeasure at the actions of targeted countries, as well as to warn of more severe consequences.
Collaboration with other groups. Additionally, Killnet has been observed to collaborate with other pro-Russia hacktivist groups; Xaknet and F*cknet both announced plans to work with Killnet in March and May 2022, respectively. Together, they have conducted “joint operations” to take down various government sites and other CII.
HOW CAN ORGANISATIONS GUARD AGAINST KILLNET?
The conflict has seen the unprecedented and extensive participation of hacktivists groups such as Killnet. These actors are unpredictable, generally answer to no overall authority and are focused on building their reputation as hackers, by racking up disruptions or defacements of the online assets of combatant states.
In the case of pro-Russia hacktivist groups, their main tactic so far appears to be causing disruption via DDoS attacks. So, what can organisations do in these conditions? Organisations should adopt appropriate prevention measures and ensure to remain vigilant, monitoring for attacks and mitigating them accordingly. Examples of measures include configuring enterprise networks with request rate limits and setting up a Web Application Firewall; organisations should also update their firewall configurations with the latest data. Organisations that require so may also consider purchasing cloud-based DDoS protection services, which alleviates the pressure of DDoS attacks onto the cloud. Organisations are advised to approach security consultants for a more tailored approach for their infrastructure. Lastly, in the event of a DDoS attack, they can also reach out to their respective ISPs for assistance.
For further details and mitigation measures, please refer to SingCERT's advisory on actions to strengthen your cybersecurity posture amidst developments in the Russia-Ukraine conflict.
SOURCES INCLUDE:
Checkpoint, CISecurity, Digital Shadows, Forescout, Intel471, Mandiant, Norton, Security Intelligence, The Washington Post, Wired.
[1] A Distributed Denial-of-Service (DDoS) attack is an attempt to use a collection of compromised computers (or botnet) to flood a system such that its service goes down or is slowed down temporarily.
[2] In networking, multiple “layers” form the computer networking protocol. Each layer is crucial to the process of transmitting data and has its own weaknesses and mitigations; hence organisations must account for the security of all layers.
[3] VK, or VKontakte, is a Russian online social media and social networking service.
[4] This refers to Lithuania’s decisions to close train routes in and out of Russia’s Kaliningrad exclave, cutting off supply of steel and other metal products.