Linked By An Unstable Bridge
Published on 05 Jul 2022 | Updated on 05 Jul 2022
CyberSense is a monthly bulletin by CSA that spotlights salient cybersecurity topics, trends and technologies, based on curated articles and commentaries. CSA provides periodic updates to these bulletins when there are new developments.
OVERVIEW
Notwithstanding the collapse in cryptocurrency values, or ‘crypto crash’ that the world witnessed in May 2022, 2021 was a phenomenal year for digital currencies. Cryptocurrency market capitalisation peaked at three trillion US dollars, and the market value of major cryptocurrencies – such as Bitcoin and Ethereum - hit all-time highs. However, the rapidly expanding cryptocurrency ecosystem also attracted the attention of cybercriminals. Among their exploits, the Ronin bridge heist of March 2022 attracted the most attention, not only because it was the largest cryptocurrency-related theft in history – with 614 million US dollars stolen, but it also underscored the vulnerabilities of a lesser-known part of the cryptocurrency ecosystem – the cross-chain bridge. With this edition of CyberSense, we will learn about what cross-chain bridges are, its general weaknesses, and some key takeaways.
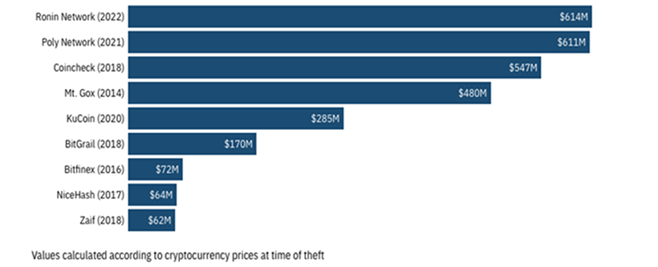
Figure 1: Top nine biggest cryptocurrency-related thefts by estimated losses as of March 2022. Source: TechMonitor
CROSS-CHAIN BRIDGES – A CRUCIAL LINK IN THE CRYPTOCURRENCY ECOSYSTEMAlthough the actual cryptography underlying the blockchains has often been described as unhackable, poor implementation of the blockchains themselves may result in vulnerabilities that leave them susceptible to simple cyber-attacks, such as phishing, social engineering, etc. This has been most evident with cross-chain bridge hacks, where more than 1 billion US dollars’ worth of cryptocurrencies had been stolen from across seven separate incidents in less than a year.
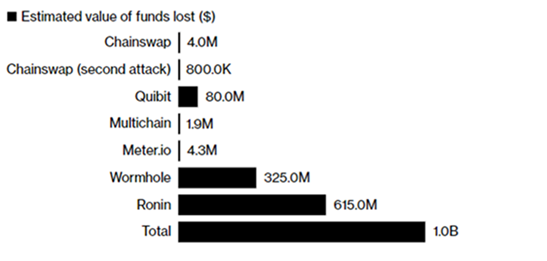
Figure 2: Top nine biggest cryptocurrency-related thefts by estimated value of funds lost as of March 2022. Source: Bloomberg
Theoretically, blockchains are designed to be immutable, tamper-proof and ‘democratic’, largely achieved through their decentralised structure – where consensus has to be garnered across all computers on the blockchain for any transaction made. As a result of this increased visibility and transparency, it is believed that fraud could be reduced. Additionally, cryptography provides an added layer of protection to blockchain data, by ensuring that no one could tamper with the data once it is added to the chain.
In reality, however, the best designed blockchain applications can fail, if they have not been developed and executed properly. Cross-chain bridges are a case in point. They lack a large development community, and their code tends not to have undergone the same rigorous checks for potential bugs as more established blockchain applications – such as the very cryptocurrency networks that they connect. This is often also compounded by the weaker governance typically found with cross-chain bridges, such as fewer validators or entities required to sign-off on any deposit or withdrawal from the network. Hence, such blockchains offer an easier intrusion vector into lucrative cryptocurrency ecosystems, and are correspondingly, targeted by more hackers.
At the ecosystem level, several experts have also concluded that cross-chain bridges can represent a single point of failure. Drawing an analogy to roads, cross-chain bridges can be imagined as poorly built, wobbly bridges connecting cryptocurrency super-highways - representing a weak link within the ecosystem. While cryptocurrencies were previously only dependent on the security validation of its native blockchain, they now also become reliant on the security verification of their cross-chain bridges. This heightens the contagion risk for the cryptocurrency ecosystem, as a cyber-attack on any given bridge could have a domino effect across the board (i.e. impacting the cryptocurrencies connected to the bridge).
Case study - Ronin cross-chain bridge hack This cautionary tale begins in early 2021, when Vietnamese firm Sky Mavis moved its popular online video gameAxie Infinity off the Ethereum blockchain and onto their in-house network called Ronin. This was intended to speed up transactions and to remove expensive Ethereum transaction fees (also known as ‘gas fees’) that its players had to contend with when trading their assets. Connected to the Ethereum blockchain via Ronin – which was also a cross-chain bridge – the latter was hacked in March 2022, resulting in a loss of 614 million US dollars. The root cause for the exploit was poor governance. First, Ronin only required a handful of its already tiny pool of validators to sign off on the transactions – only five out of its nine validators, versus Ethereum’s 300,000 validators – making it far more manageable for hackers to wrest control of the number of required accounts. This mistake was also duly acknowledged by Ronin which admitted that the “small validator set…made it much easier to compromise” their network. 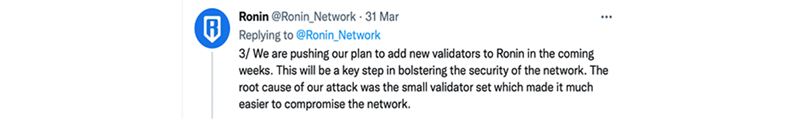
Figure 3: Ronin’s tweet about the hack in March 2022. Source: Twitter. Second, Ronin’s authentication process was not sufficiently rigorous. This hack did not exploit specific software vulnerabilities, but used social engineering techniques (interestingly, the details of the actual trick were not revealed by the company) to take over the validator accounts. More importantly, it also underscored the fact that the hackers did not require deep technical expertise to obtain such a large bounty, should their targets have poor security governance. That the hack went unnoticed and was only discovered days later - after a player was unable to make a withdrawal – also spoke volumes of the rigour of the firm’s monitoring protocol. |
BLOCKCHAIN AND ITS APPLICATIONS ARE ONLY AS GOOD AS IT IS SECURE
As blockchain and its applications (such as cryptocurrencies) go mainstream, it is easy to be caught up in the fanfare surrounding its innovation and seemingly immense potential to yield significant returns for its users – whether it be via a play-to-earn cryptocurrency game (e.g. Axie Infinity) or cryptocurrency trading. Apart from the trading risks however, investors should also be aware of the security risks – which may originate from the application as well as its associated solutions, such as cross-chain bridges, as demonstrated above.
So how can we protect ourselves, if we are determined to wade into the world of decentralised finance? The key is to be aware of its associated risks and to perform due diligence to research the companies, their tokens, and associated solutions, including their cybersecurity practices before investing. The best way forward is to take a “buyer-beware” attitude and go over the prospect with a fine comb – and ensure that their entire ecosystem isn’t being linked by a shaky, unstable bridge!
[1] This digital ledger records all transactions across a network of computer systems. It is decentralised as participants confirm all the transactions without a central authority.
[2] A method that stores and transmits sensitive information in a manner that cannot be read or accessed by anyone, except its intended recipient.
SOURCES INCLUDE:
BBC, Bloomberg, Chainalysis, CoinDesk, CoinTelegraph, CryptoVantage, Harvard Business Review, Forbes, MIT Technology Review, Norton, PwC, Quantstamp Labs, Reuters, Tech monitor, Tech Target, Twitter, Wired, World Economic Forum.