Cybersecurity Labelling Scheme (CLS) For Manufacturers
Mutual Recognition with Finland
Mutual Recognition with Germany
1 It is to be noted that CLS labels obtained through mutual recognition partnerships are not valid for use towards applications for other schemes. As an example, a developer who has attained the Cybersecurity Label from Traficom would be eligible to attain the CLS Cybersecurity label through the mutual recognition partnership. However, the developer shall not use the granted CLS label to apply for Germany’s IT Security Label.
Cybersecurity Levels & Assessment Tiers
The CLS comprises of four cybersecurity levels, corresponding to the number of asterisks on the label, as well as the highest assessment tier that the product has successfully completed.
There are four different tiers of assessment. Each assessment tier, to be completed in sequence, reflects the increasing resistance the product has to basic attacks that they may be commonly subjected to.
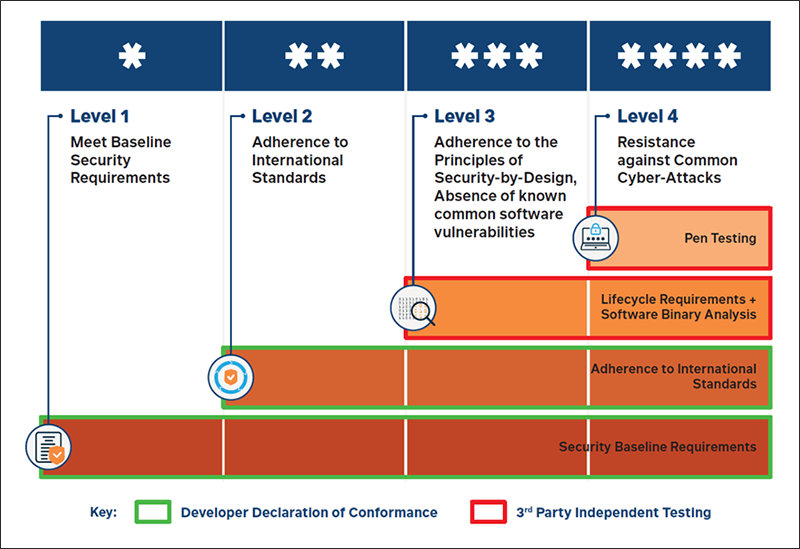
For example, manufacturers may choose to have the product rated at CLS Level 3 (three asterisks), and hence have the product undergo assessments at Tiers 1, 2, and 3.
Tier 1: Security Baseline Requirements
Manufacturers should follow a set of baseline security requirements based on ETSI EN 303 645[1] in the devices by eliminating ‘common mistakes’ to guard against majority of attacks based on common weakness such as default password, ensuring the availability of security updates and implementing means to manage vulnerability reporting.
Tier 2: Lifecycle Requirements
Manufacturers should ensure adherence to a set of International Standard (based on all mandatory requirements within the ETSI EN 303 645[1] ) in the devices.
Tier 3: Software Binary Analysis
Manufacturers should include security considerations, which are based on the IMDA IoT Cyber Security Guide[2]
, into the development lifecycle of the connected device to adopt security best practices (threat modelling, secure engineering approach, secure supply chain, security testing, and etc) to ensure security in the device. In addition, the software of the connected device is evaluated by a test laboratory using automated binary analysers to ensure that there is no known critical software weakness, vulnerabilities, or malware.
Tier 4: Penetration Testing
The connected device undergoes penetration testing by a test laboratory to provide a basic level of resistance against common cybersecurity attacks.
[1]
Cyber Security for Consumer Internet of Things: Baseline Requirements, ETSI EN 303 645, outlines 14 broad security provisions and seeks to address the most common security problems.
[2] IMDA IoT Cyber Security Guide, March 2020. The guide seeks to provide baseline recommendations, foundational concepts for IoT.